搜索结果: 1-15 共查到“modular”相关记录207条 . 查询时间(0.093 秒)

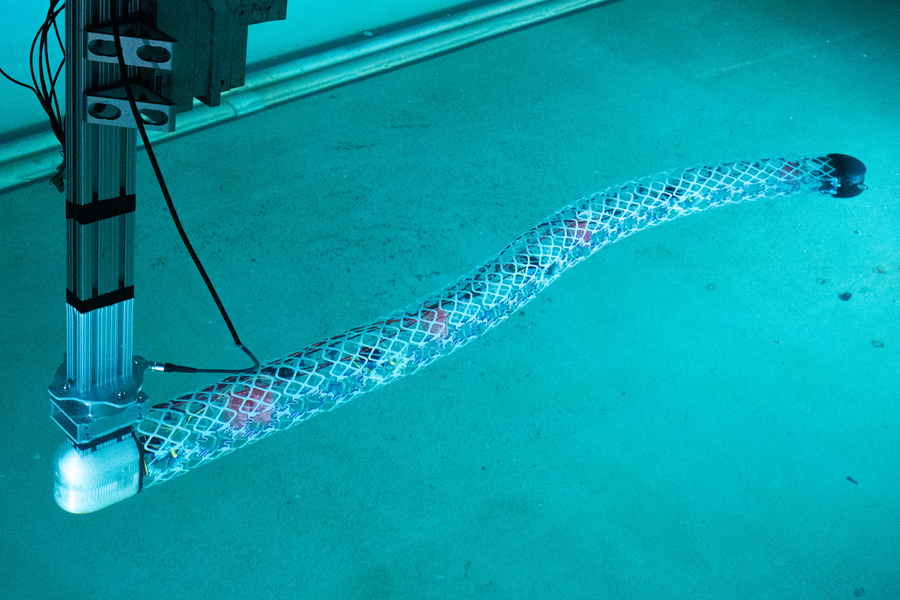
Engineers devise a modular system to produce efficient, scalable aquabots(图)
水上机器人 重复元件 模块化系统 工程师设计
2023/6/19
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:Arithmetic mixed Siegel-Weil formulas and modular forms of arithmetic divisors
算术混合 西格尔-威尔公式 算术除数 模形式
2023/5/5
SKIVA: Flexible and Modular Side-channel and Fault Countermeasures
Bitslicing Side-channel attacks Fault attacks
2019/7/8
We describe SKIVA, a customized 32-bit processor enabling the design of software countermeasures for a broad range of implementation attacks covering fault injection and side-channel analysis of timin...
New Results on Modular Inversion Hidden Number Problem and Inversive Congruential Generator
Modular inversion hidden number problem inversive congruential generator lattice
2019/6/3
The Modular Inversion Hidden Number Problem (MIHNP), introduced by Boneh, Halevi and Howgrave-Graham in Asiacrypt 2001, is briefly described as follows: Let MSBδ(z)MSBδ(z) refer to the δδ most signifi...
A Modular Treatment of Blind Signatures from Identification Schemes
Blind signature identification schemes Forking Lemma
2019/3/6
We propose a modular security treatment of blind signatures derived from linear identification schemes in the random oracle model. To this end, we present a general framework that captures several wel...
LegoSNARK: Modular Design and Composition of Succinct Zero-Knowledge Proofs
zero knowledge implementation zk-SNARKs framework
2019/2/26
We study the problem of building SNARKs modularly by linking small specialized “proof gadgets" SNARKs in a lightweight manner. Our motivation is both theoretical and practical. On the theoretical side...
Multi-Protocol UC and its Use for Building Modular and Efficient Protocols
Building Modular Efficient Protocols
2019/1/26
We want to design and analyze protocols in a modular way by combining idealized components that we realize individually. While this is in principle possible using security frameworks that provide gene...
Some Properties of Modular Addition
modular addition partitions differential cryptanalysis
2018/11/20
In this paper we study a problem which emerged during an attempt to apply a differential cryptanalysis method to the <<Magma>> algorithm. We obtained a general formula of distribution in the differenc...
LWE Without Modular Reduction and Improved Side-Channel Attacks Against BLISS
LWE problem lattice-based cryptography side-channel analysis
2018/11/19
Our interest in studying this problem stems from the side-channel attack against the BLISS lattice-based signature scheme described by Espitau et al. at CCS 2017. The attack targets a quadratic functi...
SoK: Modular and Efficient Private Decision Tree Evaluation
Privacy-preserving protocols secure computation homomorphic encryption
2018/11/16
Decision trees and random forests are widely used classifiers in machine learning. Service providers often host classification models in a cloud service and provide an interface for clients to use the...
Revisiting Single-server Algorithms for Outsourcing Modular Exponentiation
modular exponentiations secure outsourcing
2018/11/2
We investigate the problem of securely outsourcing modular exponentiations to a single, malicious computational resource. We revisit recently proposed schemes using single server and analyse them agai...
Faster Modular Arithmetic For Isogeny Based Crypto on Embedded Devices
public-key cryptography Embedded Devices
2018/9/6
We show how to implement the Montgomery reduction algorithm for isogeny based cryptography such that it can utilize the "unsigned multiply accumulate accumulate long" instruction present on modern ARM...
SIDH on ARM: Faster Modular Multiplications for Faster Post-Quantum Supersingular Isogeny Key Exchange
Post-quantum cryptography SIDH SIKE
2018/8/2
We present high-speed implementations of the post-quantum supersingular isogeny Diffie-Hellman key exchange (SIDH) and the supersingular isogeny key encapsulation (SIKE) protocols for 32-bit ARMv7-A p...
Hide The Modulus: A Secure Non-Interactive Fully Verifiable Delegation Scheme for Modular Exponentiations via CRT
Verifiable and secure delegation modular exponentiations cloud security
2018/7/9
Security protocols using public-key cryptography often requires large number of costly modular exponentiations (MEs). With the proliferation of resource-constrained (mobile) devices and advancements i...


