搜索结果: 1-15 共查到“build-up”相关记录105条 . 查询时间(0.062 秒)





New findings reveal how neurons build and maintain their capacity to communicate(图)
神经元 神经细胞 钙通道
2023/6/5


MIT expands research collaboration with Commonwealth Fusion Systems to build net energy fusion machine, SPARC(图)
英联邦聚变系统公司 能量聚变机 SPARC 聚变发电厂
2023/6/19

Social bacteria build shelters using the physics of fingerprints(图)
Social bacteria shelters using physics of fingerprints
2020/12/18
Forest-dwelling bacteria known for forming slimy swarms that prey on other microbes can also cooperate to construct mushroom-like survival shelters known as fruiting bodies when food is scarce.Now, a ...
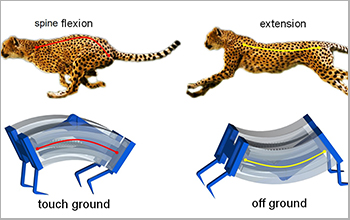
Inspired by cheetahs, researchers build fastest soft robots yet(图)
Inspired cheetahs researchers fastest soft robots
2020/5/22
Inspired by the biomechanics of cheetahs, National Science Foundation-funded researchers have developed a new type of soft robot that is capable of moving more quickly on solid surfaces or in the...

Inspired by cheetahs, researchers build fastest soft robots yet(图)
Inspired by cheetahs researchers soft robots yet
2020/5/29
Inspired by the biomechanics of cheetahs, National Science Foundation-funded researchers have developed a new type of soft robot that is capable of moving more quickly on solid surfaces or in the...

Researchers build microscopic biohybrid robots propelled by muscles,nerves(图)
microscopic biohybrid robots propelled muscles nerves
2019/10/18
Researchers have developed soft robotic devices driven by neuromuscular tissue that triggers when stimulated by light -- bringing scientists one step closer to autonomous biobots.Teams led by Taher Sa...
How to leverage hardness of constant degree expanding polynomials over R to build iO
public-key cryptography Obfuscation
2019/9/16
In this work, we introduce and construct DD-restricted Functional Encryption (FE) for any constant D≥3D≥3, based only on the SXDH assumption over bilinear groups. This generalizes the notion of 33-res...
Pseudorandom functions are traditionally built upon block ciphers, but with the trend of permutation based cryptography, it is a natural question to investigate the design of pseudorandom functions fr...
How to leverage hardness of constant-degree expanding polynomials over $\mathbb{R}$ to build iO
FE Indistinguishability Obfuscation
2018/11/6
DD -restricted FE allows for useful evaluation of constant-degree polynomials, while only requiring the SXDH assumption over bilinear groups. As such, it is a powerful tool for leveraging hardness tha...


